Oct 30, 2025Ravie LakshmananBrowser Safety / Vulnerability
A extreme vulnerability disclosed in Chromium’s Blink rendering engine could be exploited to crash many Chromium-based browsers inside a couple of seconds.
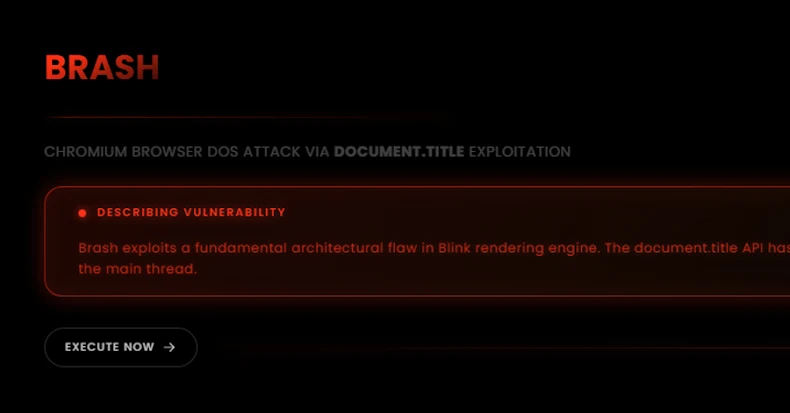
Safety researcher Jose Pino, who disclosed particulars of the flaw, has codenamed it Brash.
“It permits any Chromium browser to break down in 15-60 seconds by exploiting an architectural flaw in how sure DOM operations are managed,” Pino mentioned in a technical breakdown of the shortcoming.
At its core, Brash stems from the shortage of charge limiting on “doc.title” API updates, which, in flip, permits for bombarding hundreds of thousands of [document object model] mutations per second, inflicting the online browser to crash, in addition to degrade system efficiency because of devoting CPU assets to this course of.
The assault performs out in three steps –
Hash era or preparation part, the place the attacker preloads into reminiscence 100 distinctive hexadecimal strings of 512 characters that act as a seed for the browser tab title modifications per interval in order to maximise the impression of the assault
Burst injection part, the place bursts of three consecutive doc.title updates are executed, injecting roughly 24 million updates per second in default configuration (burst: 8000, interval: 1ms)
UI thread saturation part, the place the continual stream of updates saturates the browser’s predominant thread, inflicting it to go unresponsive and requiring pressured termination
“A vital function that amplifies Brash’s hazard is its capacity to be programmed to execute at particular moments,” Pino mentioned. “An attacker can inject the code with a temporal set off, remaining dormant till a predetermined precise time.”
“This kinetic timing functionality transforms Brash from a disruption software right into a temporal precision weapon, the place the attacker controls not solely the ‘what’ and ‘the place,’ but additionally the ‘when’ with millisecond accuracy.”
This additionally signifies that the assault can act like a logic bomb that is configured to detonate at a selected time or after a sure period of time has elapsed, all whereas evading preliminary inspection or detection. In a hypothetical assault situation, all it could take is a click on of a specifically crafted URL to set off the conduct, resulting in unintended penalties.
The vulnerability works on Google Chrome and all internet browsers that run on Chromium, which incorporates Microsoft Edge, Courageous, Opera, Vivaldi, Arc Browser, Dia Browser, OpenAI ChatGPT Atlas, and Perplexity Comet. Mozilla Firefox and Apple Safari are proof against the assault, as are all third-party browsers on iOS, on condition that they’re all primarily based on WebKit.
The Hacker Information has reached out to Google for additional touch upon the findings and its plans for a repair, and we are going to replace the story if we hear again.