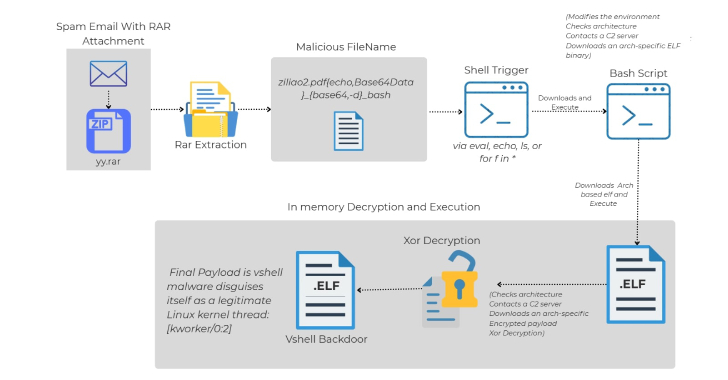
Dec 03, 2025Ravie LakshmananVulnerability / Cloud Safety
A maximum-severity safety flaw has been disclosed in React Server Elements (RSC) that, if efficiently exploited, might end in distant code execution.
The vulnerability, tracked as CVE-2025-55182, carries a CVSS rating of 10.0.
It permits “unauthenticated distant code execution by exploiting a flaw in how React decodes payloads despatched to React Server Operate endpoints,” the React Staff stated in an alert issued right now.
“Even when your app doesn’t implement any React Server Operate endpoints, it might nonetheless be susceptible in case your app helps React Server Elements.”
In response to cloud safety agency Wiz, the problem is a case of logical deserialization that stems from processing RSC payloads in an unsafe method. Consequently, an unauthenticated attacker might craft a malicious HTTP request to any Server Operate endpoint that, when deserialized by React, achieves execution of arbitrary JavaScript code on the server.
The vulnerability impacts variations 19.0, 19.1.0, 19.1.1, and 19.2.0 of the next npm packages –
react-server-dom-webpack
react-server-dom-parcel
react-server-dom-turbopack
It has been addressed in variations 19.0.1, 19.1.2, and 19.2.1. New Zealand-based safety researcher Lachlan Davidson has been credited with discovering and reporting the flaw on November 29, 2025.
It is price noting that the vulnerability additionally impacts Subsequent.js utilizing App Router. The difficulty has been assigned the CVE identifier CVE-2025-66478 (CVSS rating: 10.0). It impacts variations >=14.3.0-canary.77, >=15, and >=16. Patched variations are 16.0.7, 15.5.7, 15.4.8, 15.3.6, 15.2.6, 15.1.9, and 15.0.5.
That stated, any library that bundles RSC is more likely to be affected by the flaw. This contains, however shouldn’t be restricted to, Vite RSC plugin, Parcel RSC plugin, React Router RSC preview, RedwoodJS, and Waku.
Wiz stated 39% of cloud environments have situations susceptible to CVE-2025-55182 and/or CVE-2025-66478. In mild of the severity of the vulnerability, it is suggested that customers apply the fixes as quickly as potential for optimum safety.